ENS One of the core developers was the target of the attack and this crypto currency It shows how vulnerable investors are. This trap, where even professionals can be reduced, can cause serious losses for a significant part of crypto currency investors. So what are the details of the incident? What should investors pay attention to?
Google deficit and crypto currencies
Cyber attackers continue their efforts to gain unfair profits with all kinds of methods. Fake product advertisements, artificial intelligence -supported so -called investment opportunity videos, viruses, fishing attacks should be extremely cautious in order to avoid grievances.
ENS Core developer Nick crypto- It is a name known by the community and fell into the trap established by attackers using two vulnerabilities that have not yet been resolved in the Google infrastructure.
“I have recently been the target of an extremely sophisticated identity hunting attack and I want to emphasize it here. This attack benefits from a security vulnerability in Google’s infrastructure, and it is likely that we can see such attacks more often because they refuse to correct this gap. Here is the e-mail that comes to me;”
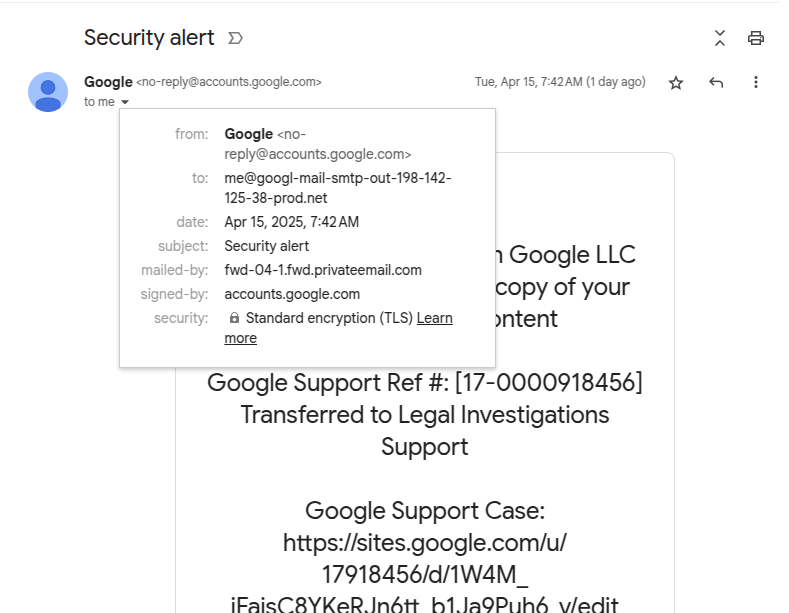
“The first thing to consider is that this is a valid and signed e-mail-really sent at No-Reply@Googlecom. Dkım passes signature control and Gmail displays it without any warning-even puts it to talk to other legitimate security warnings.”
DKIM (Dominx Idedied Mail) is a safety protocol that confirms the identity of the e-mail and guarantees that the e-mail is not changed on the road.
Details of the attack
To increase the credibility of the fake website GoogleThe attackers who take advantage of the site feature can easily trap their victims to the first shock. Sites connection takes you to a very convincing “support portal” page. The attackers who take advantage of Google Altomain product push the victim to log in to his account.
“It works as follows: First, they save a domain name and create a Google account for ‘me@domain’. The domain name is not so important, but it helps to look like a kind of infrastructure. As you will see soon, the choice of ‘I’ is clever.
Then, one Google Oauth they create the application. For the name of the application, * enters the entire text of identity hunting message – new lines and all – then a large number of spaces and “Google Legal Support”.
OAUTH gives permission to ‘ME@…’ address. They allow access to Google account. This creates a ‘Security Warning’ message sent from Google to ‘ME@…’ e-mail addresses. Since Google creates the e-mail, it is signed with a valid DK switch and passes through all controls.
Finally, they transmit the message to their victims. Since I only confirm the message and titles and confirms the envelope, the message passes the signature verification and appears as a legal message in the user’s incoming box – even in the same message series with legal security warnings.
Since Google calls ‘me@’, Gmail indicates that the message is sent to me at the top; This is the abbreviation he uses when a message is sent to your e-mail address-avoids another indicator that can send red flags.
I sent an error report to Google; Unfortunately, they closed it as ‘it works as it is aimed’ and explained that they did not see it as a security error. Frankly, I do not agree – but be careful against deceptive security warnings from Google until they change their ideas. ”
This is complex hack The method seems to be used by more professional attackers. But the average Crypto currency investors As the method becomes widespread, it can be the goal. Therefore, make sure you are on the original website and login page by checking the address bar several times in all your login operations. Check everything a few times before you read and take action that excites you (a lawsuit filed, will be closed, etc.) that may cause you to have eye illusion with small letters changes.
In addition, do not use the e -mail address you use on stock exchanges as much as possible, and know that complex mail addresses of letters and numbers are more likely to be targeted in possible attack mails.
Responsibility Rejection: The information contained in this article does not contain investment advice. Investors should be aware that crypto currencies carry high volatility and thus risk and carry out their operations in line with their own research.








